Energy providers are among the most important operators of critical infrastructures (CRITIS). A supply failure has far-reaching consequences for the economy and consumers. The primary goal is to ensure a secure and continuous supply, smooth operation, and the protection of the environment and people.
Why security is important for energy providers
Energy providers have complex, interconnected infrastructures and consist of many different facilities, which can also be located in remote areas, such as offshore wind farms. This structure makes them more vulnerable to acts of sabotage, vandalism, and cyberattacks.
Supply security bottlenecks, fines, or issues with regulatory compliance are just some of the potential risks. Additionally, there is the issue of data security and the responsibility to protect the environment and people. This necessitates the demarcation of particularly sensitive areas. Comprehensive security strategies are important as they help reduce the risk of virtual and physical attacks, all with the aim of maintaining availability, integrity, and confidentiality.
Providers of the energy industry *
Electrical supply:
- Generation
- Transmission
- Distribution of electricity
Gas supply:
- Promotion
- Transport
- Fuel and heating
Petroleum and oil supply:
- Crude oil production
- Product manufacturing
- Oil transport
- Fuel and heating oil supply
District heating supply:
- Generation
- Distribution of district heating
Source: Classification of sectors and critical services according to the Federal Office for Civil Protection and Disaster Assistance, as of July 20
Interflex Access Control:
Flexibility and Security for All Applications

Protection Against Sabotage, Accidents, and Unauthorized Access in Power Plants
Locations: Power plants (nuclear, fossil, renewable energy generation)
Suitable Solutions:
- Multi-factor authentication with modern ID methods (LEGIC advant, Mifare DESFire EV3), key app on the smartphone (3-pass authentication), and PIN codes at access terminals.
- Biometric solutions ranging from fingerprint 2D/3D verification to facial, iris, and hand vein recognition.
- Evacuation management with a dynamic evacuation list for a quick real-time overview of the people to be evacuated.
Your Benefits:
- By effectively preventing or hindering access by unauthorized persons, you reduce your risk of sabotage, damage, and potential liability issues.
- At the same time, you comply with your security regulations. Accidents are effectively avoided, and your personnel are protected when only trained staff gain access to particularly secure areas.
- In the event of an evacuation, you also ensure the protection of your personnel and enable targeted, efficient deployment of firefighting forces.
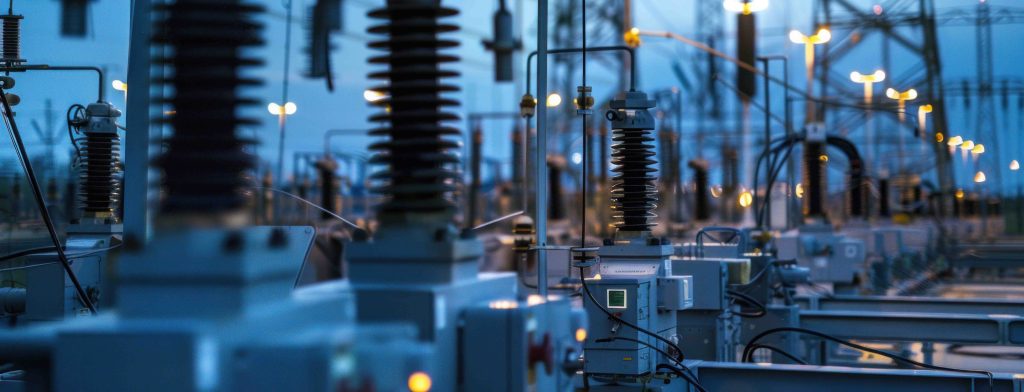
Protection Against Power Outages or Damage in Substations and Switchgear
Locations: Substations and switchgear (for the distribution and transmission of energy)
Suitable Solutions:
- Invitation portal for external companies to securely manage access rights for external companies and suppliers, such as service technicians for maintenance and repairs.
- Multi-level approval workflows: secure, location- and time-limited rights assignment for authorized external and company personnel.
Your Benefits:
- Relieve your security organization with a high degree of automation in granting access rights, especially if your critical facilities are managed or monitored decentrally.
- Through seamless documentation in rights management, you are always able to provide information when rights assignments are reviewed as part of an audit.
- In the event of a security incident, you can quickly trace who received rights, when, and for what purpose. This allows you to identify security gaps in physical security for the future and effectively comply with new security requirements.

Protection of Sensitive Data and IT Infrastructures in Office Buildings and Data Centers
Locations: Office buildings and data centers
Suitable Solutions:
- Scalable system IF-6040: Definition and cross-organizational control of access rights, access profiles, and room zones. Secure logging and monitoring of all events of the access control system in one system, such as door status monitoring and anti-passback.
- Encrypted, certificate-based PKI communication with Interflex’s own certificates or with customer-specific encryption.
- Visitor management with the IF-6040: Standardized process from invitation, reception, identity verification to safety instructions and documentation of visits.
Your Benefits:
- A flexible and adaptable security solution allows you to respond promptly to changing security requirements or personnel needs.
- The high level of encryption enables you to comply with new security requirements.
- Traceability in the event of a security incident and during audit checks is simplified when there is seamless documentation of access rights assignments or external visits.
Secure Your Business:
5 Steps to a Reliable Access Control System
Analysis
Comprehensive analysis of your security requirements and existing systems
Planning
Development of a tailored security concept
Installation
Installation and configuration of the relevant components
Handover
Training for safe handling of your system
Support
Regular and reliable service and support
That’s why customers choose Interflex:
Frequently Asked Questions about the Energy Industry
Do you have any questions? We are happy to help you!
To reach the appropriate contact person at Interflex, please select the suitable contact method. If you are already a customer, kindly use the Contact form ”I am an Interflex customer” and get in touch with the desired department via email.
If you haven’t had any previous interactions with Interflex but are interested in our solutions, we would be pleased to receive your inquiry through the Contact form ”I am interested in becoming a customer” We will endeavor to respond to you promptly.
Do you have a question, require information, or wish to share feedback with us? Please select the relevant department for your inquiry:

Service:
For technical questions and error reports, please send an email to:


Feedbackmanagement:
Would you like to provide us with feedback? Please feel free to send us an email to:



