Access control ∙ access control systems ∙ electronic ∙ biometric ∙ On-Premise or Cloud-based
Overview of Access Control
Whether in research departments, data centers, or administrative buildings, access control determines who is allowed in and who is not, wherever sensitive information, equipment, or people need protection. It establishes clear boundaries, safeguards what is valuable, and provides transparency and control over all entry points, automatically, reliably, and with full documentation.
Modern access control systems go far beyond simply opening doors. They dynamically manage permissions, record and log access events without gaps, and integrate flexibly into existing processes. They should also meet current standards in terms of procedures and encryption technologies. Whether wired online, wireless, offline, or enhanced with biometric methods, Interflex offers solutions tailored to every security requirement.
What Is Access Control?
Definition of Access Control
Access control encompasses all security measures and procedures aimed at regulating physical access to specific areas and preventing unauthorized entry. Various identification methods are used for this purpose, including RFID technologies such as LEGIC® advant or MIFARE® DESFire, biometric features like fingerprints, iris scans, facial recognition, or hand vein patterns, as well as mobile solutions via smartphone (e.g., NFC, Bluetooth, or QR code/PKPass). Multi-factor methods, such as combining a reader with a PIN or biometrics with mobile credentials, can also be flexibly integrated. Modern systems allow for flexible rights assignment, log all access events completely, and support compliance requirements.
A modern access control system should reliably fulfill three key aspects:
- Assignment of access permissions: It must be clearly defined who is granted access, when, and why.
- Compliance: It must be traceable who granted access permissions to whom and when.
- Logging of access events: It must be documented who accessed which area, when, and where.
Main Objectives of Access Control
The primary goals of access control are to protect people, assets, and information, prevent unauthorized access, and ensure traceable management and logging of all access events. It helps organizations implement tailored security requirements and comply with regulatory standards.
Why Is Access Control Important?
In highly regulated industries such as chemicals, pharmaceuticals, healthcare, food production, energy providers, and government agencies, there are especially strict requirements for security, traceability, and the protection of sensitive areas. Interflex offers reliable solutions that not only meet these demands but also simplify workflows.
Access Control with a System
A modern access control system should do more than protect. It should be intelligent. Interflex solutions adapt to your security infrastructure, integrate seamlessly into existing processes, and grow with your organization and its needs. Whether at production sites, laboratories, or administrative buildings, access rights with Interflex can be managed not only individually but also efficiently, across locations, scalable, and without media disruptions.
Logging Access Events Clearly and Securely:
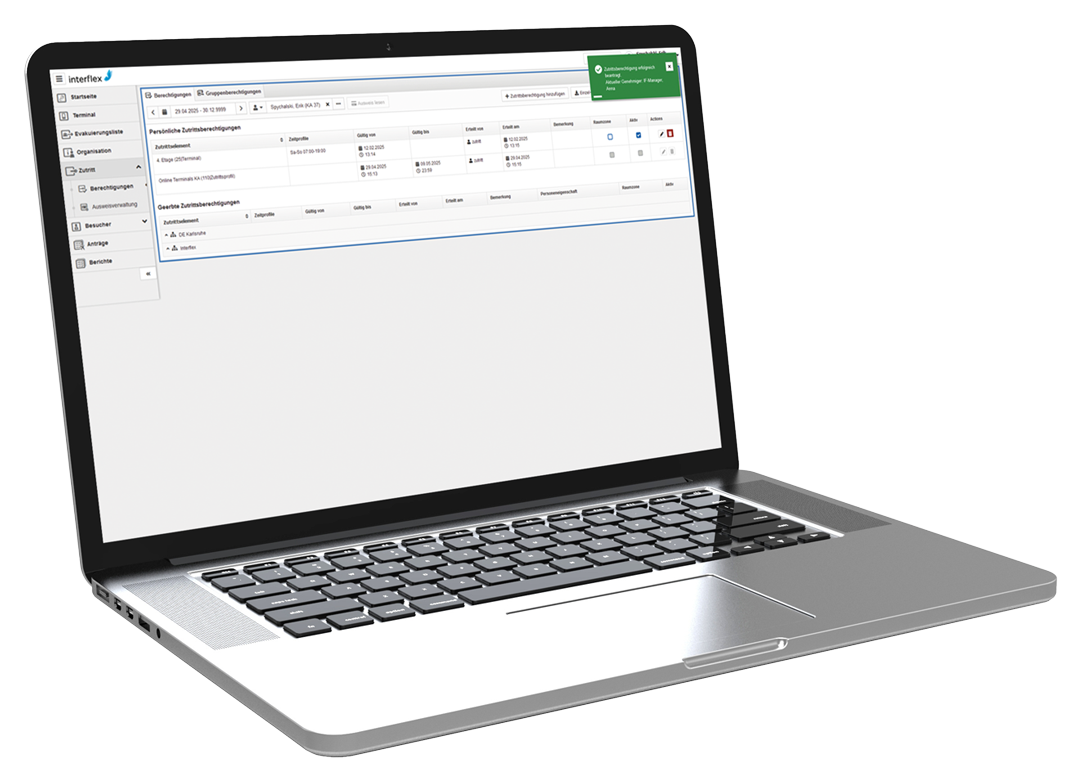
With the Interflex system IF-6040, you receive powerful and reliable software that enables you to implement complex security requirements with ease. The software provides a transparent and centralized overview of all access events, even across multiple locations. It ensures that all entries through connected terminals and locking components are logged in a tamper-proof manner down to the second and recorded and stored in compliance with data protection regulations (GDPR).
On the application side, all changes to access permissions can also be reliably tracked. This allows IF-6040 to support companies in meeting internal reporting obligations, compliance requirements, and external audit demands.
Today’s Requirements
Digitalization, flexible work models, a shortage of skilled workers, outsourcing, and increasing security regulations are presenting companies with new challenges. Security-critical industries in particular require systems and solutions that can represent complex authorization concepts in a secure and legally compliant way.
Architectures and Standards - Security Technology with Vision: With the Interflex platform IF-6040, complex authorization concepts can be mapped based on personal attributes such as users, roles, and profiles. This form of user management enables clear separation and secure processing of data. The solution can also be operated in a multi-client environment and integrated into security architectures according to the guidelines of the BSI-IT baseline protection or the ISO/IEC 27001 standard. High security standards are already taken into account during software development through the principles of Security by Design and Security by Default.
Industry Solutions
Manufacturing Industry: Companies in the manufacturing sector use Interflex to secure their production areas with precisely defined access zones for warehouses, machinery, and sensitive operational areas. Temporary access permissions for suppliers and partners can be requested, managed, and granted securely through visitor management processes, with all access movements monitored and controlled.
Automotive: In the automotive industry, companies protect sensitive development and testing areas with repeated access checks and secured zones for administration and production. Access control systems use role-specific access rights, which can be combined with elevator control and time tracking. This ensures that only authorized personnel gain access and project confidentiality is maintained.
Government and Public Institutions: Access to public buildings requires reliable separation between employees and public visitors. Access control measures such as turnstiles, electronic card readers, or professional visitor management systems allow targeted control and monitoring of access to specific areas.
Energy Providers: Control centers and substations require the highest level of protection to ensure uninterrupted operations. Interflex solutions, combined with two-factor authentication or biometric access control, offer a high level of security. Remote facilities can be integrated into a centralized security concept using modern electronic access control solutions.
Finance: Banks and insurance companies rely on finely tuned access rights, for example, for temporary project teams during mergers or renovations. Tamper-proof logging of access events meets the requirements of internal auditors and external regulatory authorities.
Pharmaceuticals: Laboratories, production sites, and storage areas are sensitive zones subject to strict GMP (Good Manufacturing Practice) standards to maintain high quality. Access control ensures that only qualified and authorized personnel can enter these areas through precise management and logging of access events.
Types of Access Control Systems
Which Solution Fits Your Business?
Access control systems differ in their technical architecture, operating mode, and identification method. Interflex offers modern electronic and biometric solutions, either standalone or combined, for every application.
The Interflex solution goes far beyond the functions of a traditional locking system. Electronic locking systems are a simple and practical solution for access control. In contrast, the access control solution is a powerful and scalable system that not only manages door access but also integrates into larger security and building management systems. This makes it ideal for complex and large organizations that require high security and centralized management.
Electronic Access Control Systems
Electronic systems form the foundation of modern access control. They are based on RFID technologies or mobile credentials and can be divided into two main categories: offline systems and online systems.
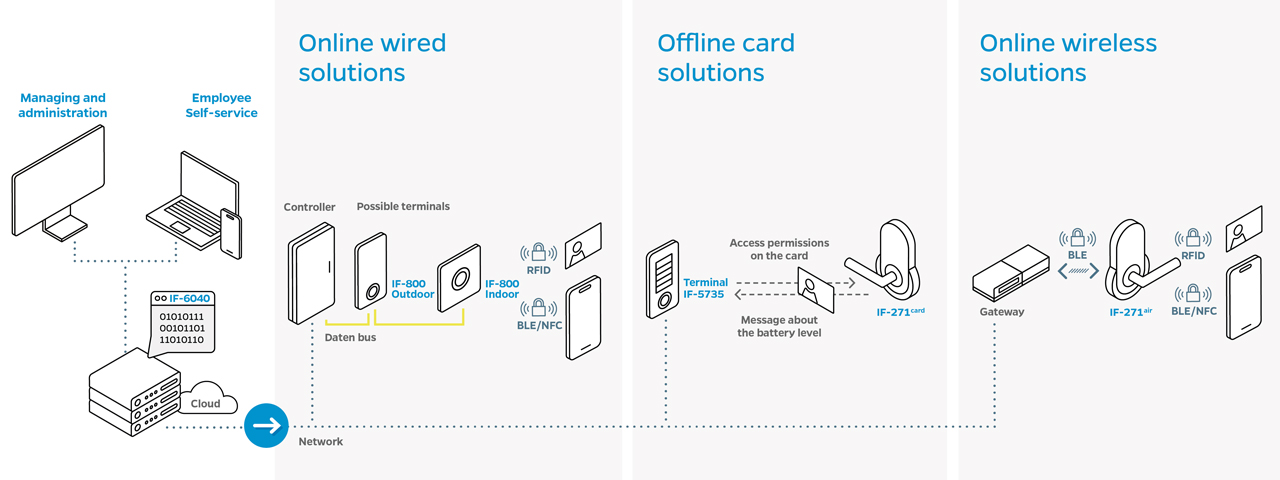
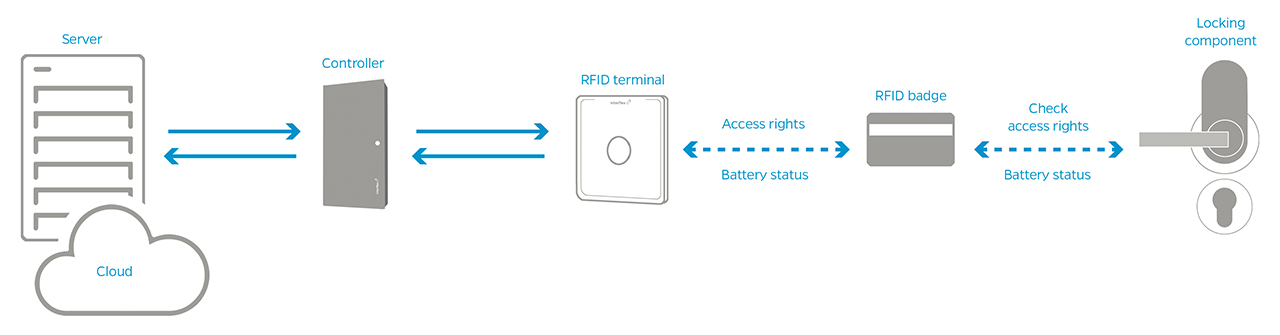
Offline Access Control Systems
In offline systems, access rights are stored directly on the identification medium. This makes them a reliable solution, especially for locations without a permanent network connection or for remote sites. The readers operate independently and are an excellent modern alternative to purely mechanical locking systems. They serve as a contemporary replacement for traditional keys.
When combined with the NetworkOnCard concept (a form of virtual networking), a high level of security and centralized rights management can be achieved even without a constant system connection. Typical areas of use include smaller buildings, storage facilities, archives, or meeting rooms.
Online Access Control Systems
Online systems are connected to central control software and enable real-time processing of access events as well as cross-site management. They can be further categorized into wired and wireless variants:
Online Wired Access Control Systems
Wired systems are connected to central control software via a network. Access events are processed immediately and logs are stored instantly. These systems are particularly suitable for large companies, critical infrastructure, and regulated industries with high security requirements. Due to their reliability, they are especially well suited for high-traffic access points.
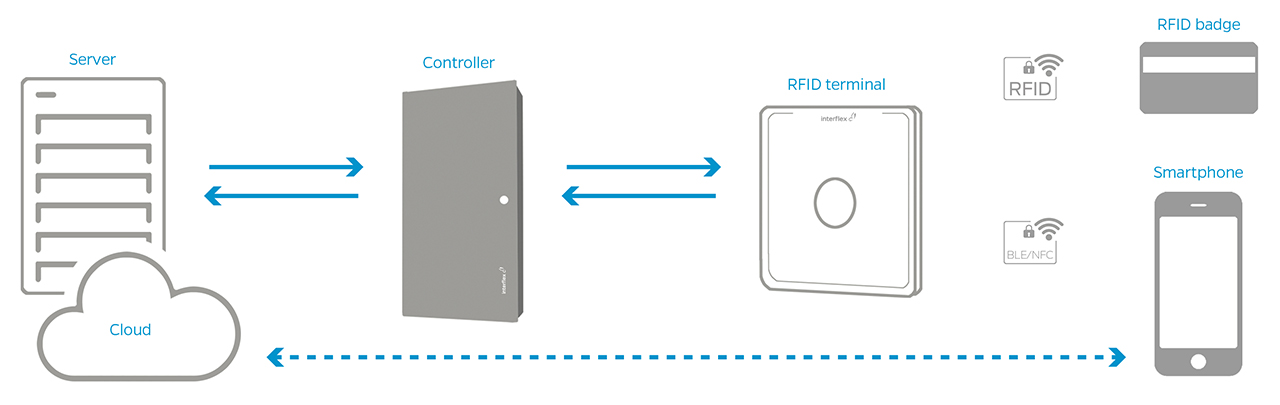
Online Wireless Access Control Systems
Wireless systems offer maximum flexibility and can be integrated quickly and easily into existing infrastructures. They are ideal for locations without a power supply or where installation would be complex. Access rights are managed centrally through the control software, and permissions can be granted or revoked at any time.
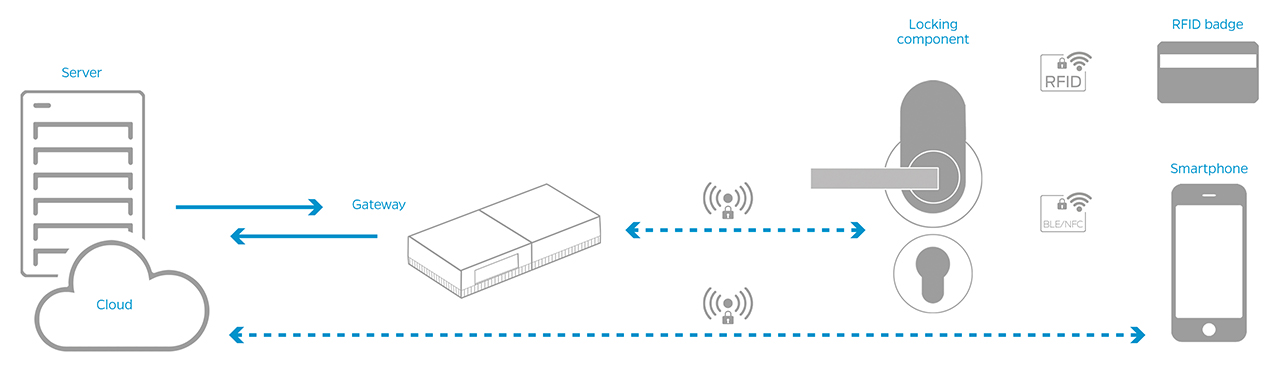
Special Types of Access Control
Biometric Systems
Identification is based on physical characteristics such as fingerprints, facial features, iris scans, or hand vein patterns. Biometric systems can be seamlessly integrated into electronic access solutions and offer particularly high security for sensitive areas such as data centers, research facilities, laboratories, or control rooms.
Visitor Management
As a complementary access module, Interflex’s visitor management enables structured and reliable administration of access permissions for service providers, suppliers, and visitors—from invitation and registration to check-out. It helps reduce the workload at your reception desk. With features for personalized visitor passes (such as QR codes or wallet passes) and modules for conducting safety briefings, document verification (ID check), or issuing replacement credentials, Interflex offers a professional and end-to-end solution for transparent and secure visitor processes.
Cloud-Based Access Control Systems
In cloud-based access solutions, the central software system is operated entirely or partially in the cloud. With its Cloud Services, Interflex provides a secure and scalable platform for managing and controlling your access permissions, including software, hosting, and ongoing support. Cloud solutions are especially suitable for companies that, for cost or capacity reasons, do not wish to maintain their own infrastructure but still require a high level of security and flexibility, such as those with distributed locations.
Diverse Technologies from Interflex – Customizable to Your Needs
Interflex offers all modern access control systems from a single source, from cloud-based platforms and online networked solutions to biometric identification methods. The systems can be flexibly combined and precisely tailored to your building structure, security levels, and user groups, whether you want to secure individual doors or manage international locations centrally.
Opendor – Flexible Locking Components
The Opendor product line, available in Air and Card versions, includes electronic locking components such as door fittings, handles, cylinders, and locker locks. These components are available in both offline (Card) and online wireless (Air) variants and can be seamlessly integrated into the IF-6040 access control system.
The battery-powered devices allow for easy and cost-effective retrofitting without wiring. Thanks to support for RFID and Bluetooth® Low Energy (BLE), a wide range of identification media can be used. The components utilize state-of-the-art, certificate-based security protocols that meet current technological standards. An integrated decision-making logic also ensures uninterrupted operation in the event of a system failure, such as a lost wireless connection to the host.
Comparison Table
Which Access Solution Fits Your Requirements?
The following table provides an overview of the key features of different access control systems. Whether wired, wireless, offline, biometric, or cloud-based, compare functions, areas of application, and investment levels to find the solution that best matches your infrastructure and security goals.
An Overview of Our Solutions
A comprehensive access control system is not just about powerful software or reliable hardware – it’s about the perfect interaction between both. Interflex offers you coordinated solutions that support your security strategy effectively and ensure long-term investment protection.
Software and Cloud Services - Manage Access Digitally and Centrally
With Interflex software solutions, you can efficiently manage access rights, processes, and evaluations. Operation can be either on-premise or in the cloud. Our software is scalable, audit-proof, and easily integrates into existing IT environments thanks to open interfaces and support for common standards.
Your Advantages:
- A 360-degree solution for access control, visitor management, and time tracking or workforce management
- Centralized rights management based on:
- Organizational units (e.g., departments)
- Personal attributes (e.g., role, manager, external employee)
- Time parameters (e.g., specific hours or weekdays)
- Spatial zones (e.g., security areas, specific floors, individual offices)
- Intuitive operation via web-based self-service interfaces (accessible in accordance with BITV 2.0)
- Customizable workflows with multi-level approval processes for targeted access rights assignment
- Open interfaces and supported standards (e.g., OpenAPI REST, OpenID Connect) for ERP, HR, and IT systems
- Flexible operating model: on-premise or cloud-based
- Supports compliance with data protection regulations (GDPR)
- Investment protection through backward compatibility and expandability
- Made in Germany: development, operation, and support from a single source
Detailed System Information from Interflex:
Access rights can be easily assigned and managed using the “IF-6040 Access” system based on the following criteria:
- Organizational units (e.g., departments, plants)
- Personal attributes (e.g., role, external company, management level)
- Time parameters (e.g., time of day, shift model, weekdays)
- Spatial zones (e.g., security areas, floors, buildings)
Access profiles are centrally managed in IF-6040, automated, and location-independent – fully tailored to your specifications and requirements. The key goal is to simplify and optimize complex security processes, allowing you to focus on your core security responsibilities.
Even small adjustments to access profiles can lead to significant changes in your overall authorization concept. For example, if an employee changes their organizational unit, the system automatically assigns them the access rights of their new department or location. If an employee is deactivated because they are no longer with the company, all access rights can be revoked instantly with just a few clicks.
Defined self-service workflows support targeted access rights assignment, enabling employees to request additional permissions as needed and for a limited time. All approvals are fully documented, ensuring high levels of security, transparency, and traceability across your organization.
Terminals and Components - Secure Access Implementation
Whether for doors, turnstiles, factory gates, or vehicle access points – Interflex provides the right access readers and identification technologies for every application, both indoors and outdoors. Our terminals, readers, and scanners are robust, highly secure, and easily integrated.
Features and Equipment at a Glance:
- Extensive portfolio of access readers for RFID, QR codes, and BLE/NFC for mobile credentials
- Multifunctional terminals with or without PIN entry and touchscreen options
- Biometric devices for secure identification using 2D/3D fingerprint recognition, as well as facial, iris, or hand vein scanning
- License plate recognition for automated vehicle access control at barriers and loading zones
Modern Authentication Technologies - Smart and Secure: Interflex systems support multi-credential management and the combination of different authentication methods depending on the application and access point. Identity features are processed in a pseudonymized manner. Supported methods include:
- RFID badge (optionally with PIN entry for added security)
- Fingerprint scanner (2D and 3D)
- Facial recognition, iris scanner, and hand vein scanner
- Mobile identification via the Interflex Key App (including “Shake to Open,” geofencing, and BLE long-range booking) - also usable on wearables like the Apple Watch
Badge Management in Detail – Efficient and Aligned with Your Corporate Identity: RFID and mobile badges with layouts tailored to your corporate design – with Interflex’s solution, access credentials can be created, personalized, and printed with just a few clicks. The system supports the creation and management of replacement credentials and enables cross-site and cross-media access rights management. Visitor management also becomes especially efficient: visitor badges can be prepared in advance, permissions granted with just a few clicks, centrally managed, and quickly revoked after the visit ends.
Your Advantages
- Automated processes with minimal administrative effort
- Transparency and traceability for audits and reviews
- Cross-site and cross-media badge and replacement management
- Customizable layouts in line with your corporate design
- Wide range of supported media: RFID badges, key fobs, chips, mobile credentials (e.g., via Wallet), QR codes (visitor passes), and PKPass solutions for visitors
Monitoring and Reporting - Systematic Oversight: Dashboards, alert functions, rights monitoring, and audit-proof reports – automated, exportable, and compliant with audit standards. Additionally, events at access points can be visualized in real time and linked to alarm functions if needed. Ideal for security control centers or centralized monitoring rooms.
Critical Infrastructure and Industry-Specific Solutions
Interflex’s access control solutions support compliance with the requirements of NIS2 and the CRITIS umbrella law. This makes them particularly well-suited for environments where the highest security standards must be met. At the same time, they simplify the work of security officers by streamlining complex security structures and processes, making them more transparent and efficient. These solutions can also be easily adapted to changing requirements and different company sizes.
For companies operating in critical infrastructure sectors (CRITIS), they are an ideal component of both digital and physical security strategies. As a long-standing partner to medium-sized and large enterprises, Interflex offers industry-specific solutions for sectors such as energy, water, healthcare, IT and telecommunications, food, logistics and transportation, media, municipal waste management, finance, as well as public administration and government institutions.
Critical Infrastructure-Ready – Certified Security for the Highest Demands:
Interflex is certified according to ISO/IEC 27001:2013 and ISO 9001:2015. Our solutions comply with EN 60839-11-2:2015 and support data protection requirements (GDPR). We are a member of the German Federal Office for Information Security’s “Alliance for Cybersecurity.”
From the very beginning of software development, we apply design principles such as Security by Design and Security by Default. In addition, the security level of each current version of our IF-6040 software is regularly verified through independent security tests (penetration tests).
Looking to implement, expand, or optimize your access control system?
Use our contact form to send us your questions. Our dedicated team will get back to you as soon as possible.